
SSL vs TLS: Decoding the Differences
SSL and TLS are cryptographic protocols gaurantee data privacy, authenticity, and integrity over a …

7 Most Common Programming Errors Every Programmer Should Know
Every programmer encounters programming errors while writing and dealing with computer code. They m…

Difference Between Array and String
Many programming languages, such as C, C++, Java, etc., support an array and a string. While an arr…
Difference Between While and Do While Loop
Loops come in handy when you want to execute the same block of code repeatedly. They help you optim…

Unlocking the Phases of Ethical Hacking: A Comprehensive Guide
Although the term hacking in ‘ethical hacking’ may confuse you as an illegal practice, …
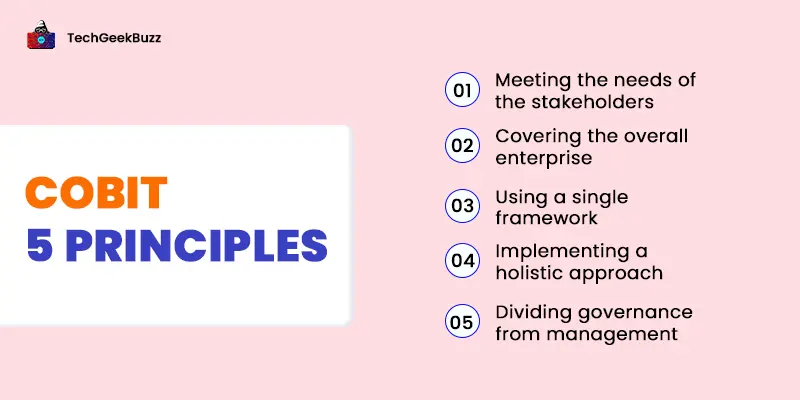
COBIT 5 Principles - Everything You Need to Know About!
Imagine a bus without a conductor. Directionless, right? To bring in order, structure, and directio…
What is Data Breach? Proactive Steps for Robust Protection
Data privacy is one of the hottest topics of recent times. COVID-19 has forced most businesses to o…

20 AI Tools That Can Replace Your Team of 10 People
Artificial intelligence has left no field untouched, and this term is now familiar to most people. …
![What is a White Hat Hacker? [Definition, Tools, & Techniques]](/media/new_post_images/White_Hat_Hacker.webp)
What is a White Hat Hacker? [Definition, Tools, & Techniques]
When people hear the word "hacker," they often imagine a stereotyped gloomy figure—…

Introduction to Elixir Programming Language
We know that website development is at its tipping point, as most businesses aim to go digital nowa…

Linear Programming - Definition, Types, and Applications
Optimization plays a vital role in every aspect of our lives. From managing problems at the workpla…
![What is an Assembler? [Definition, Working, & Types]](/media/new_post_images/What_is_Assembler.jpg)
What is an Assembler? [Definition, Working, & Types]
Like a compiler and interpreter, an assembler is a language processor that accepts the as…
