Although the term hacking in ‘ethical hacking’ may confuse you as an illegal practice, it is not.
It is simply a process of providing digital safety to your digital world.
Our lives are majorly intertwined with technology. Hence, the need for opting for safe measures is crucial. As you must be aware, the cyber menaces, such as cyberattacks, data breaches, or online threats, are rapidly increasing. This is where ethical hacking comes into the picture. In this world, skilled professionals use their expertise to shield us from such unwanted cyber-attacks.
Do you know, as per a report, ethical hackers were able to explore over 65,000 vulnerabilities in 2022 alone?
In this article, I will delve into the concept and different phases of ethical hacking. Let’s start!
What is Ethical Hacking?
Ethical hacking is also known as white-hat hacking. It is simply a systematic approach that helps you to address and identify the security vulnerabilities in your systems or networks.
The primary goal of ethical hacking is to avoid any loopholes that may lead to malicious attacks, potentially destroying your infrastructure.
It is important to notice that ethical hackers always work with authorization. This ensures that they are not involved in any illegal hacking activities.
There are three major types of ethical hacking, as mentioned below:
- Black box testing : In this type of testing, the tester does not know the network or system prior.
- White box testing : The tester is completely aware of the system or network infrastructure and its workings.
- Gray box testing : The tester is somewhat aware and somewhat not about the system he is testing.
Ethical hacking is a continuous process and not a day’s work. The organizations must conduct regular assessments to check for possible system vulnerabilities.
5 Different Phases of Ethical Hacking
As mentioned below, there are five main types of phases in ethical hacking.
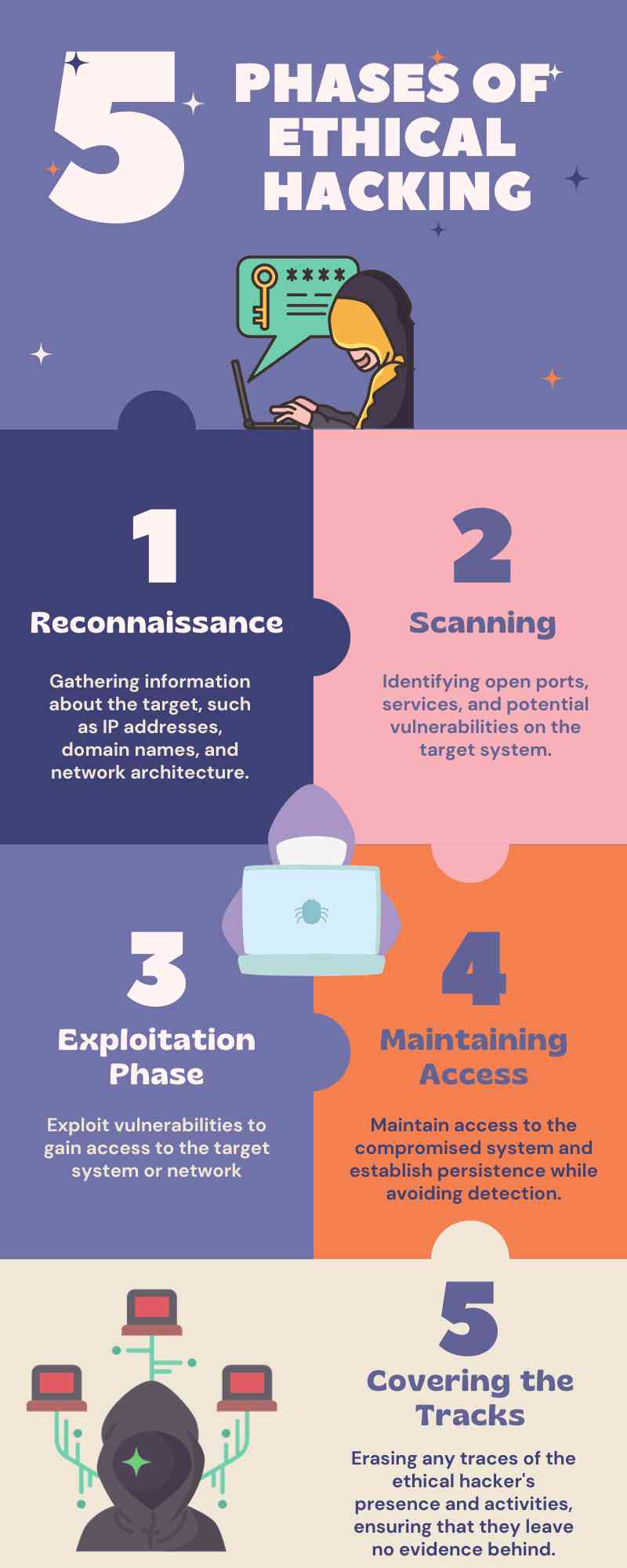
1. Reconnaissance
Reconnaissance is also termed footprinting and is basically a preparatory phase.
In this step, the hacker focuses on the target and gathers as much information as possible. Ethical hackers find the vulnerabilities, track the credentials, and aim to hack the system. Additionally, ethical hackers focus on meticulous documentation during the reconnaissance phase, such as email addresses, domain names, IP addresses, etc.
The reconnaissance phase is broadly divided into 2 types:
- Passive Reconnaissance : Through this approach, ethical hackers obtain information without directly communicating with the target. They retrieve available sources like DNS records, websites, social media, etc.
- Active Reconnaissance : This approach aims to find information by direct interactions with the target. Ethical hackers use methods like DNS enumeration or network scanning.
Note : in this phase, the ethical hackers get critical insights into the target ecosystem. This helps them to know about the probable vulnerabilities and security weaknesses.
2. Scanning
After retaining the information of the target system, the next step is to scan tools and techniques to know their vulnerabilities. They actively check the services or open ports to know more about the target.
Ethical hackers also build a network topology map using the information retrieved in the scanning phase. This includes network devices and their security bottlenecks or relationships between systems.
Port scanning is a crucial part of the scanning phase.
- It consists of sending network packets to the IP address of the target on different code numbers to check the status of ports (open, closed, filtered).
- Once the hackers identify open ports, they try to decode the services running on them. This can provide valuable data about the configuration and versions of services.
Note : The scanning phase provides a complete understanding of the security system of the target system/network.
3. Exploitation Phase
The exploitation phase is also known as the gaining access phase in ethical hacking. As you can see, the hackers focused on finding the vulnerabilities in the previous steps. So, in this phase, they attempt to exploit them and enter into the target’s system. Here are a few exploitation techniques that ethical hackers follow in this step:
- They capture the public exploits that are easily available (pre-existing vulnerabilities).
- If they do not find public exploits, they create custom exploits to benefit from the vulnerabilities.
- After getting access, ethical hackers try to reach higher level credentials so as to bring the system more under their control.
- A higher level of access can ensure easy access to sensitive data.
Note : After gaining the access phase, the ethical hackers prepare a report including a detailed account of exploited vulnerabilities, all the methods, and potential outcomes.
4. Maintaining Access
Ethical hackers must maintain the previously gained access. It helps them to scrutinize the target system properly due to the continued access. The aim of this phase in ethical hacking is to retain their presence so as to fetch more vulnerabilities.
Further, hackers focus on finding out potential risks of the maintained access. They see from an attacker's lens and make assumptions about how they can harm the organization.
Moreover, some of the most commonly used techniques in this step include:
- Trojans : Trojans are malicious software set that helps maintain access by running in the background.
- Backdoors : Backdoors create secret entry points that help to enter the system repeatedly.
- Scheduled tasks : Scheduled tasks imply that hackers can set up scripts that are able to run as and when they want in case of re-establishing access.
Note : After this step is complete, the hackers discard all the persistence mechanisms and access.
5. Covering the Tracks
The ‘covering the tracks’ phase is also known as erasing tracks. This phase shows that the hackers have completed their assessment.
The primary aim of ‘covering the tracks’ is to wipe out all the evidence regarding the activities of ethical hackers. Basically, they delete all the related files that could indicate their hacking involvement.
- All the persistence mechanisms in the previous phase must be removed or disabled.
- This time also involves the alteration of artifacts. It implies that they make it tedious for others to decode the timeline of activities.
- They also perform encryption on sensitive data to protect it from being used.
- Hackers try to restore altered settings (if any).
Note : It is crucial to remember that all the activities must be carried out near laws and regulations. All the information presented by the hacker here creates the final report to understand, identify, and respond to a cyberattack.
What is the Future of Ethical Hacking?
Ethical hacking is here to stay. The demand is surely going to increase manifolds in the near future.
As cyberattacks are increasing daily, ethical hacking is gaining more importance. Every business, small or big, aims to create a safe ecosystem away from the menace of online attacks. Ethical hacking provides that safety!
The comprehensive knowledge of ethical hackers and the first-hand experience help protect employers’ systems.
As more companies are moving to the cloud, this implies that everyone needs better protection for their infrastructure. It is widely being opted in diverse fields, such as healthcare, government enterprises, banking, entertainment, etc.
Final Words
We live in a world with a thin line between security and vulnerability. Therefore, it becomes important for us to protect our digital realm with the best safety measures. As we discussed ethical hacking in depth in this article, it is an excellent solution that protects you from the bad side of the internet.
Further, the different phases of ethical hacking mentioned above help the experts assess the security of a system or network.
These are structured and systematic approaches to ethical hacking. Moreover, the organizations can take help from it and identify weak areas in their ecosystem, saving them from malicious attacks.
I hope this article helps you strengthen your knowledge base and gain valuable information.
Good luck!
People are also reading:


![What is a White Hat Hacker? [Definition, Tools, & Techniques]](/media/new_post_images/White_Hat_Hacker.webp)


Leave a Comment on this Post