In the current digital age, where the rate of cybercrimes is increasing day by day, it becomes essential for software development companies to build security into the applications they develop. As modern applications are growing more and more complex, it is leading to more security vulnerabilities that threats imposters can exploit.
So, testing modern applications for the security of their data and functionalities becomes of the utmost importance. And this is where security testing comes into the picture.
Often when it comes to software testing , we simply think of testing applications against specified requirements and quality standards. However, it is not enough. Validating applications for security before they release into the market is also of equal importance.
Among the types of software testing , security testing is one that assesses software products or applications for security issues. It involves identifying less or no secure spots in software applications and improving them to prevent intruders from exploiting them after applications become live in the market.
In this blog post, we shall introduce you to security testing in software testing, its importance, principles, types, process, myths and facts, and some widely-used tools.
What is Security Testing?
It is a kind of software testing that evaluates a software product to spot security vulnerabilities, risks, and threats and protects it from cyber threats . It makes sure that the data and resources of the software product are safe from all possible types of cyber attacks and intruders.
Moreover, security testing examines the effect when applications are provided with malicious and unexpected inputs. It provides evidence that applications do not accept any unauthorized or malicious input, making them safe and reliable.
The main goal of this kind of testing is to find any security holes or defects that can cause a significant loss of data or harm an organization's reputation. After discovering security vulnerabilities, It is simple for developers to address problems and guarantee the security of the applications.
Need for Security Testing
As discussed above, the primary purpose of this type of testing is to expose vulnerabilities in the application’s security mechanism that safeguards data and maintain their intended functioning. So, to avoid applications being compromised by threat imposters and losing confidential or private data, security testing is essential.
In this internet age, there is an immense rise in the development and usage of web applications. They are the ones that are more vulnerable to cyberattacks.
If you release a web application without testing it for security, it is more likely to be the prey of attackers. The reason is that you don’t know the spots of your application that are susceptible to attacks. And when you are unaware of this, intruders will definitely exploit those spots to make their attacks successful.
As a result, conducting security testing on web applications, as well as all other types of applications, becomes necessary.
Objectives of Security Testing
The following are the foremost objectives of security testing:
- Identifying security threats in applications.
- Measuring the potential vulnerabilities in applications.
- Spotting all possible security risks in applications.
- Fixing security all security issues through coding.
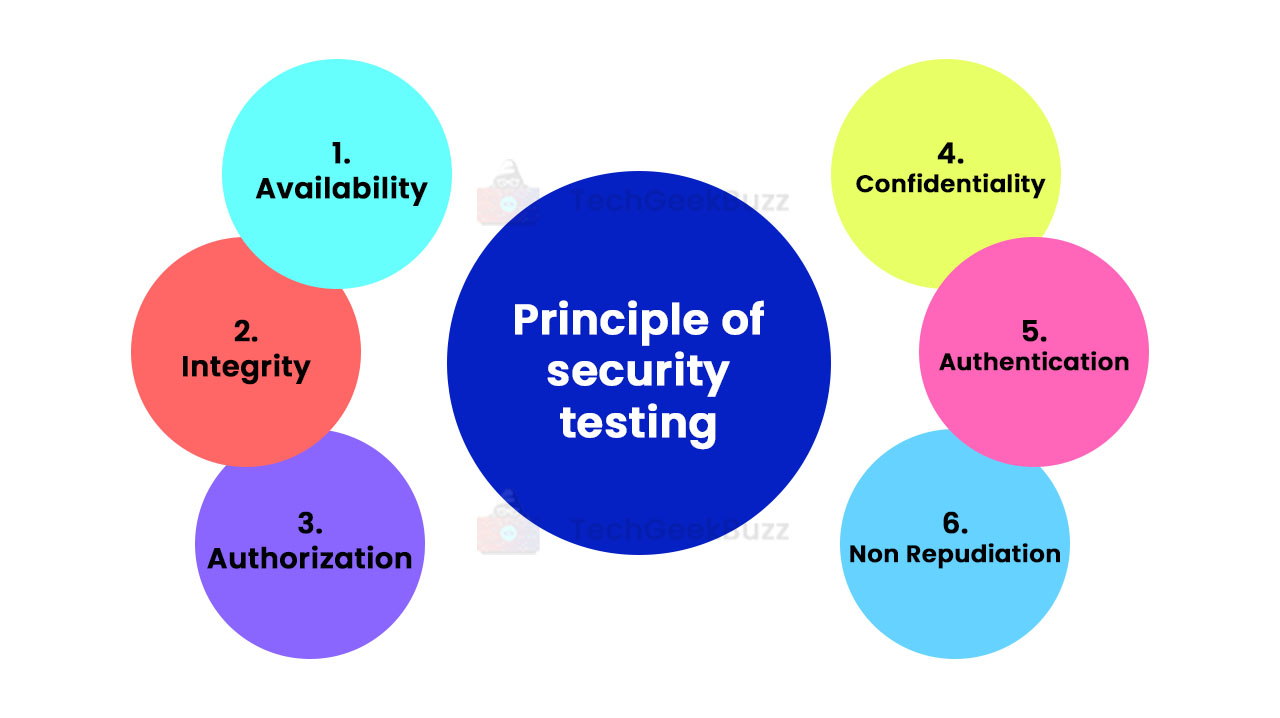
Principles of Security Testing
Now, let us discuss some major principles of security testing here.
-
Availability
This principle states that the main authority should have control over the application data, and they should make it available whenever the authorized users need or request them. To ensure the availability of data, it is important to maintain all hardware components by repairing them timely and urgently when required.
-
Integrity
This principle specifies that the data between the sender and the intended receiver should be accurate, consistent, and trustworthy. Any third party or unauthorized people should not alter data.
-
Authorization
This principle states that real or intended clients should be able to perform certain actions on the application and get back the desired service from it. The best example of authorization is access control.
-
Confidentiality
It relates to the privacy of data and entails some set of rules that restricts access to private information. It does not disclose sensitive information to unauthorized and unintended users. Hence, it avoids falling data into the wrong hands. Only people who have the right to access that data will get it.
-
Authentication
Authentication entails validating a user’s identity and making sure that the information they receive is from a legitimate source.
-
Non-repudiation
This principle specifies that the sender should not deny a request from an authorized receiver. The exchange of information between two legit parties takes place with timestamps.
Primary Focus Area in Security Testing
The following are some major areas of applications that you need to focus on while performing this kind of testing:
- Network Security: It involves checking the weaknesses and imperfections in the network structure.
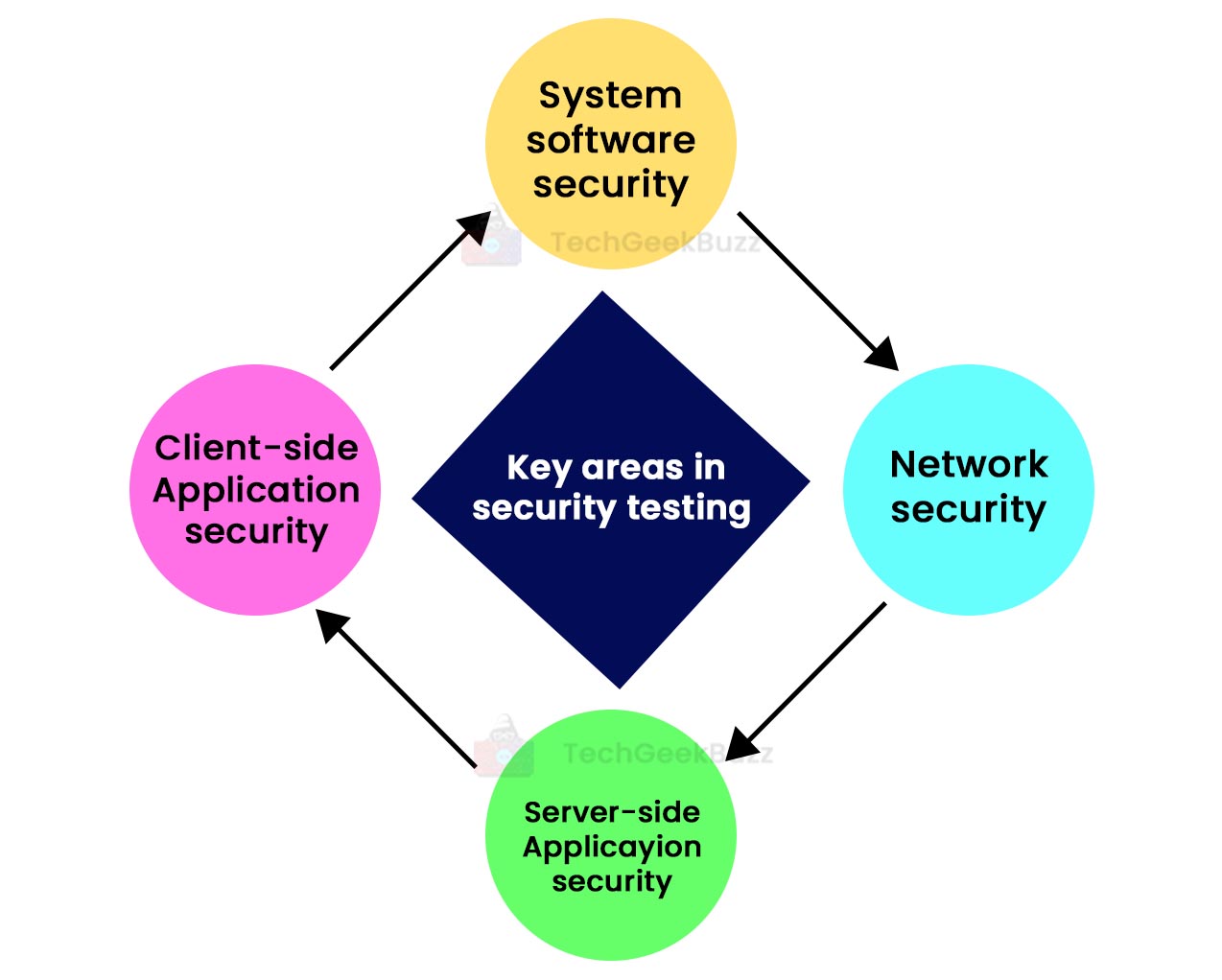
- System Software Security: It primarily focuses on testing the application and identifying weaknesses based on different types of software, such as database systems or operating systems.
- Client-side Application Security: This makes sure that threats imposters cannot run on any browser or tool that real users or customers use.
- Server-side Application Security: It ensures that the server encryption and server tools are capable of defending the application against any kind of threat or disturbance.
Types of Security Testing
The following are the different types of security testing:
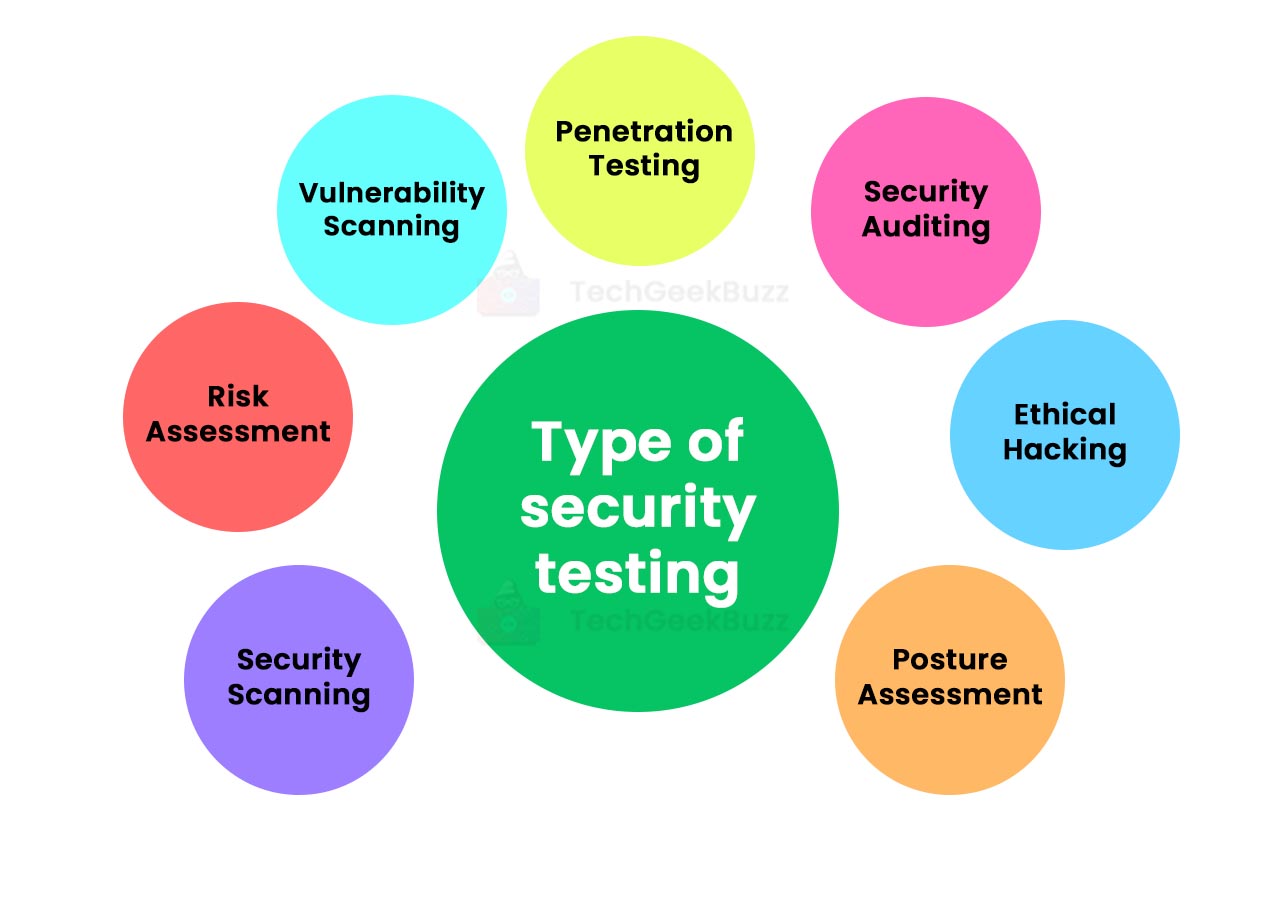
- Vulnerability Scanning: Automated software tools come in handy to perform vulnerability scanning. These tools scan the applications and look for known vulnerability patterns.
- Penetration Testing : It involves simulating the attack from malicious hackers on the applications to determine weaknesses, threats, and risks that could result in the hacking of the applications.
- Security Scanning: It is all about determining potential weaknesses in the networks and systems and providing essential solutions to fix them. You can do it either manually or using automated tools.
- Security Auditing: This type of testing involves inspecting applications and operating systems internally to spot potential defects or errors. You can perform a security audit by checking the code line-by-line.
- Risk Assessment: It entails inspecting security risks observed within an organization. These risks are divided into three levels, namely low, medium, and high. This research backs risk-reduction procedures and strategies.
- Ethical Hacking: Ethical hacking is in complete contrast with malicious hacking. It entails leveraging the same hacking techniques as intruders do but the intent is to disclose security weaknesses in the application.
- Posture Assessment: It is the combination of ethical hacking, security scanning, and risk assessment that improves the security posture of the entire organization.
How to Perform Security Testing?
This type of testing is usually carried out in the early stages of the software development life cycle (SDLC). If done after the entire development process, it costs a heavy amount.
Here is how you can perform security testing in each phase of SDLC:
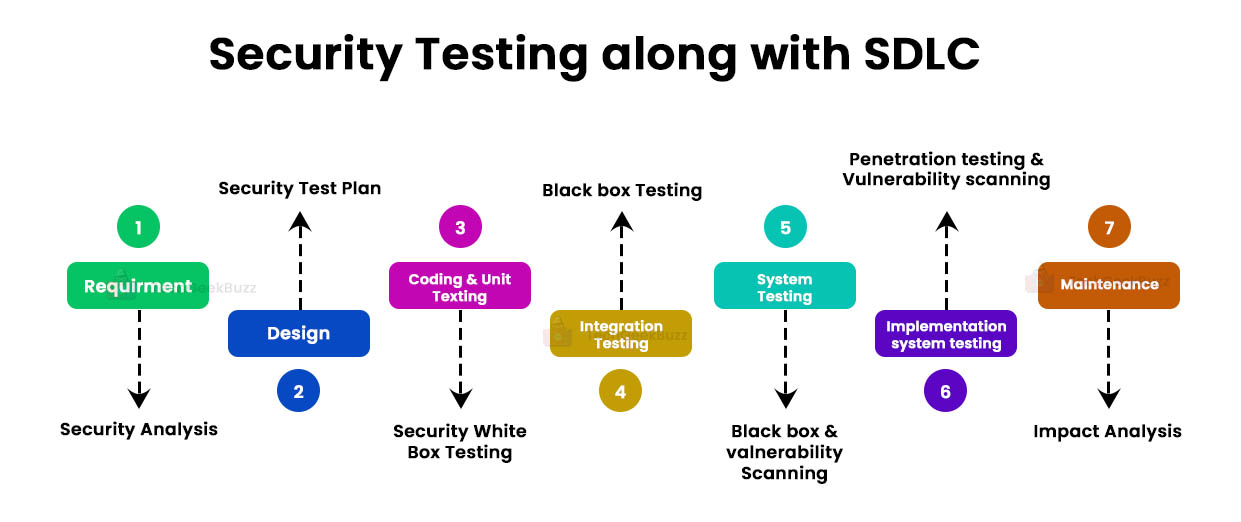
Step 1
SDLC: Requirements Phase
Security Procedure: At this stage, you need to perform a security analysis on the business requirements to verify which use cases are useful and which are waste.
Step 2
SDLC: Design Stage
Security Procedure: The design phase involves exploring the risk associated with the design of the software product under development and considering security tests during the creation of the test plan.
Step 3
SDLC: Coding Stage
Security Procedure: The coding or implementation phase entails performing white box testing as well as static testing and dynamic testing.
Step 4
SDLC: Integration Testing
Security Procedure: The testing phase involves performing black-box testing .
Step 5
SDLC: System Testing
Security Procedure: This phase involves black-box testing and vulnerability scanning.
Step 6
SDLC: System Testing Implementation
Security Procedure: This phase requires you to carry out vulnerability scanning and penetration testing.
Step 7
SDLC: Maintenance Stage
Security Procedure: In this phase, you need to perform an impact analysis of the patches.
The security test plan should include the following aspects:
- Test cases and scenarios associated with security
- Security test tools
- Security-related test data
- Analysis of test output from different test tools
Techniques for Security Testing
There are three different testing techniques, as listed below:
- Tiger Box: This testing technique requires a laptop with different operating systems and hacking tools . Security testers and penetration testers carry out vulnerability assessments on the application.
- Black Box: In this testing technique, testing professionals have the authority to validate everything about the network topology .
- Grey Box: It is an amalgamation of black and white box testing types, where testing professionals have partial knowledge of the application under test.
Test Scenarios for Security Testing - Example
Here are a few examples of test scenarios to provide you with an understanding of how security test cases should be:
- The application under test should not support any invalid user.
- The password should always be in the encrypted format.
- Verify the cookies and session time.
- In the case of financial websites, ensure that the back button does not work.
Security Testing Tools
Let us now throw light on some popular and widespread security testing tools.
This tool is perfect to find and fix vulnerabilities in your web applications quickly and easily. It combines DAST + IAST scanning to spot more than 7000+ types of vulnerabilities in your web applications, including SQL injections, exposed databases, and XSS.
With this tool, you get more than 90% of the result even before half scanning is left. It prioritizes high-risk vulnerabilities automatically. In addition, it lets you schedule your scans and allows scanning multiple environments at the same time.
It is an online scanner that scans vulnerabilities and identifies cybersecurity weaknesses in your digital infrastructure. It comes with industry-standard scanning engines that let you scan your IT stack, including private and public websites, endpoint devices, servers, and cloud systems.
Moreover, this tool scans your systems automatically for threats and vulnerabilities and secures your IT environment. It provides intelligent results that save your time in analyzing them. Besides automated scanning, this tool ensures continuous penetration testing.
-
OWASP WTE
OWASP Web Testing Environment is a collection of various application security tools and documentation. The primary goal of this project is to equip testers with a ready-made testing environment and developers and trainers to learn and hone their security skills.
Check out: Open-Source Security Testing Tools
Myths and Facts About Security Testing
When it comes to this type of software testing, there are a lot of myths associated with it. Here, we shall discuss some myths related to this testing type and the corresponding facts.
|
Myth |
Fact |
|
There is no financial profit on the application under test. |
This testing type identifies the areas in the application that can be improved and result in maximum output. |
|
Due to the increasing rate of cyberattacks, organizations adopt security hardware or software to protect their IT infrastructure. |
Instead of buying hardware or software for protection, organizations should understand security procedures and then apply them to protect their assets. |
|
Small businesses do not require security procedures. |
Every organization, whether it is small or large, needs security measures. |
Conclusion
Here ends our discussion on security testing. This type of software testing helps organizations spot and fix security vulnerabilities in the applications and prevent them from being exploited by intruders. Testing professionals mimic attackers and try to detect security loopholes with the intent of improving them. In short, this testing type ensures that end users can use applications while protecting their sensitive data from hackers.
People are also reading: