These days, humans and computing systems work closely together. Computing techniques are in use in every application. You might be curious about how businesses safeguard their data and maintain the privacy of their banking activity. The answer to each of these queries is "cryptography."
As technology is growing at a rapid pace, so does the rate of cyber threats . As a result, people are more concerned about their privacy than ever before. Along with a lot of benefits, technology also comes with potential risks that may be adverse for individuals as well as corporations. It becomes essential for them to protect their data and information from being accessible to untrusted third parties. And this is where cryptography helps.
This method has been in use to protect information for thousands of years and still continues to stay on the top. It has come a long way from the ancient Egyptian hieroglyphics and remains the most important factor in securing communication or messages or information in transit by preventing third parties from intercepting.
In this post, you will learn about the many types of cryptography and how to use them to protect your data against theft and manipulation.
Let's dive into it.
What is Cryptography?
To understand the term, let us first break it into two parts. The term "crypt-" means "hidden" or "vault," and the suffix "-graphy" means "writing." Collectively, it implies writing something that is hidden. More precisely, cryptography is a method of leveraging code to ensure secure communication such that the message transferred is able to be understood and accessible only by the person for whom it is intended.
Various mathematical concepts and algorithms form the basis for this technique that makes it possible to transform plain text into a form that is difficult to decrypt or decipher. In addition, we can use these methods and algorithms for various purposes, including creating cryptographic keys, digital signatures, data privacy assurance, web browsing, and secure email and credit card transactions.
Modern cryptography methods leverage ciphers and algorithms like 128-bit and 256-bit encryption keys to encrypt and decrypt data. Modern ciphers are impenetrable, such as the Advanced Encryption Standard (AES).
History
We can understand more about the history of cryptography by looking at one of the earliest ciphers ever used. It is known as the Caesar cipher because Julius Caesar used it for his private correspondence; according to his biographer Suetonius, "He wrote in cipher, which is when he flipped the letters of the alphabet when he wished to convey anything confidential. The fourth letter of the alphabet, which is D, must be used in place of the letter A in order to decipher them and understand what the message is.
The Caesar cipher is categorized as a substitution cipher since each letter is changed with a new one; subsequent repetitions of this could subsequently exchange letter blocks or whole words. For the majority of history, military and government communications were encrypted using a variety of substitution ciphers.
Science was progressed during the Middle Ages by Arab mathematicians, especially in the field of decryption. It became easier for scientists to identify patterns, for instance, once they realized that some letters in a language occur more frequently than others. For the obvious reason that it was difficult to perform mathematical changes quickly enough to make encryption or decryption worthwhile prior to the introduction of computers. However, by contemporary standards, the majority of ancient encryption is quite straightforward.
Charles Babbage's Difference Engine concept piqued his interest in cryptography before the development of modern computers. The Germans employed the electromechanical Enigma machine to encrypt messages during World War II. The British team led by Alan Turing is recognized for creating a similar tool to break the code and establish the foundation for some of the earliest modern computers. As computers became more accessible, cryptography became far more challenging, but for many more years, only spies and generals used it.
The Importance of Cryptography
Cryptography plays a very vital role in safeguarding data and users, maintaining confidentiality, and preventing cyber criminals from intercepting data in transit. It is present everywhere in this modern world, from securely sharing passwords to online shopping sites, bank servers, and email clients to ensuring secure communication by authenticating people and devices.
In short, we cannot imagine the modern world without cryptography. Without it, secure communication would not have been possible, which would, in turn, put people at great risk of losing their private and confidential information. It would have been possible for untrusted third parties to intercept ongoing communication between two trusted parties. In addition, bank transactions would have gone completely wrong. So, everything based on the internet would have come to a halt, leaving people’s private data in the hands of cybercriminals.
Fortunately, we have cryptography that ensures everything in this IoT-connected world goes well by preserving communication and making sure that data remains only between the two intended parties.
Cryptography Techniques
Cryptographic techniques should be a part of a multilayered security approach. Similar to how fences and door locks try to keep robbers off the property or out of a house, some security measures, including installing a firewall and using access rights, aim to keep intruders entirely outside the network or computer. Cryptography provides an internal line of protection.
Cryptography protects our data from intruders who hack into the systems. Also, not all data is shared with everyone in the company. Cryptography is a method to ensure that certain data is safe and that only specific people have access to it.
Modern-day cryptography is all about converting plain text or clear text, which is easily understandable by humans, into cipher text. This process is simply encryption. The cipher text is again transformed back into plain text, which is generally decryption.
The following are the four goals of modern-day cryptography:
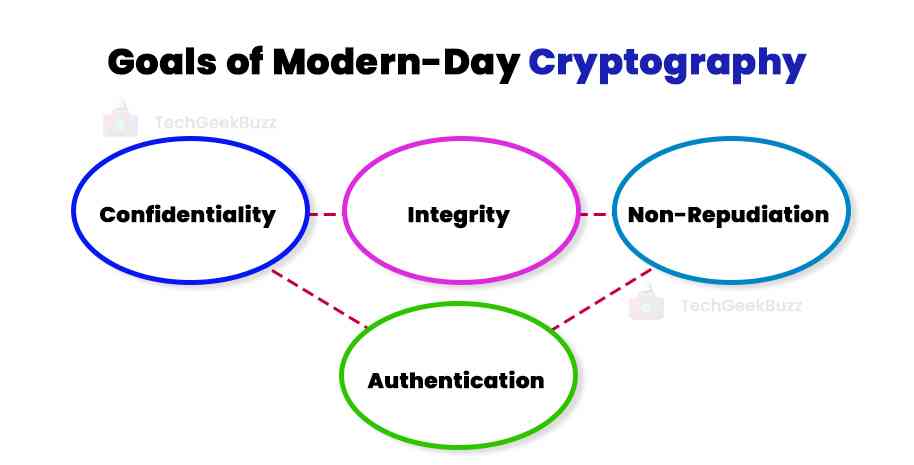
- Confidentiality: No third party can understand the message or information being transferred between two intended and trusted parties.
- Integrity: There should be no modification or alteration of messages in storage as well as transit between the sender and the intended receiver.
- Non-Repudiation: The sender is not allowed to deny later the intention of sending the message to the intended receiver.
- Authentication: The sender and receiver confirm each other's identity and the source and destination of the message being transmitted.
The protocols and procedures that comply with all the above features are cryptosystems. Cryptosystems are basically considered a collection of computer programs and mathematical procedures. However, they also have the essence of human behavior as suggesting hard-to-guess passwords, not sharing sensitive information with others, and logging off from unused systems automatically.
Types Of Cryptographic Algorithms
Cryptographic algorithms are often known as ciphers. They are simply protocols and procedures the cryptosystems leverage to encrypt and decrypt data with the aim of protecting communication between computer systems, devices, and applications.
A cipher suite employs three algorithms: one for encryption, one for message authentication, and one for key exchange. These three algorithms work out and give a secure connection or encryption. The entire process is as follows:
- The generation of public and private keys for data encryption and decryption.
- Authenticating the messages begging transferred through digital signing and verification.
- The exchange of keys.
Types Of Cryptography
Let us now shed light on the different types of cryptography.
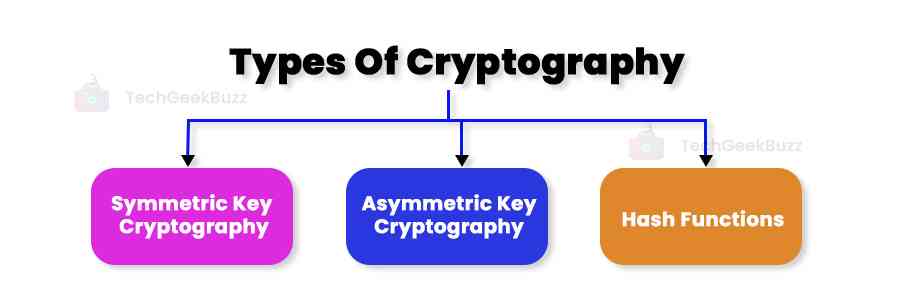
Symmetric Key Cryptography
Also known as secret key cryptography, this type encrypts data with a single key. Because this type employs the same key for encryption and decryption, it is the most straightforward type of encryption.
Using a cryptographic technique, which encrypts the data using the key in a cipher, a person with the secret key can decode the data. Private key cryptography can be helpful for both in-transit and at-rest data. Still, it is usually applied to at-rest data because in-transit data could be compromised if the message recipient learns the secret.
When using secret-key or symmetric-key encryption techniques, the sender encrypts data using the secret key, and the recipient decrypts it using the private key.
The symmetric encryption is P = D(K,E( P) )
Where,
K = Encryption and decryption key
P = Plain text
D = Decryption
E§ = Encryption of plain text.
Asymmetric Key Cryptography
Often known as public key cryptography, this type uses two keys to encrypt data. The first key encrypts the communication, while the second key decodes it.
The "private key" is the one that is a secret; the "public key" is the one that is available to everyone and is consequently known as such. Because of the mathematical link between the keys, we can derive the public key from the private key but not the other way around. The owner should be the only person with access to the private key. The public key can be accessible to any other entity.
Public-key or asymmetric-key encryption techniques encrypt data using a public key associated with the creator or sender and decrypt it using a private key that is only known to the originator.
Asymmetric encryption is P = D(Kd,E(Ke,P)).
Where,
Ke = Encryption key
Kd = Decryption Key
D = Decryption
E(Ke,P) = Plain text encryption using an encryption key
P = Plain text
Hash Functions
One-way, irreversible hash functions safeguard data at the cost of making it impossible to recover the original message. A way of transforming a given string into a string of a specific length is hashing. For each input, a good hashing algorithm will provide an exceptional result. Testing every conceivable information until you get the same hash is the only way to crack a hash. A hash is also present in certificates and data (like passwords).
What Are Cryptographic Key Attacks? What Are the Types?
Modern methods to generate cryptographic keys are becoming increasingly complex and are frequently thought impenetrable. As more businesses use cryptography to secure conversations and data, it is essential to keep keys secure. Legal action, financial penalties, brand damage, and the exclusion of clients and investors could all result from a single compromised key. It is essential to understand that there are many ways in which the key is under attack. It is necessary to safeguard these keys.
Following are the potential key-based issues and attack types to consider:
- Overusing a key, such as encrypting an excessive amount of data, makes it vulnerable to assaults. This is especially true with earlier ciphers and could lead to data exposure. Keys must be under constant changes, renewal, and updates as necessary.
- Keys are more vulnerable to attack if they are present with encrypted data. In many cases, the attackers may find the key along with the data. This can lead to much more damage.
- Cryptographic keys kept in server memory have been vulnerable to massive cyberattacks. The key should be under certain conditions and in encryption to prevent tampering. This avoids the loss of data if there is any cyber attack.
- One of the most dangerous threats to any key is an insider threat. This is most likely to happen when a rogue employee gets access to the key and then uses it for personal gains or sells it to hackers in exchange for money.
- Any key that develops a problem without a backup causes the data it protects can be lost or inaccessible. Critical life cycles must be fully captured and preserved to ensure seamless conduct of future investigations in case of key compromise.
- Keys are more vulnerable to attack or theft if crucial management procedures are manually recorded on paper or in spreadsheets since human error is possible.
- Keys are just random numbers that are harder to decipher as they get longer. The value of the data it secures and the duration for which that data is under protection are essential when determining the critical strength and length.
- Keys use a high-quality, validated random number generator that gathers noise from appropriate hardware sources and converts it into entropy, or the information density of a file in bits or characters.
- Every key should only be created once for a given encrypting or decrypting function; otherwise, it may not provide the necessary level of security.
- When keys are incorrectly encoded, hackers can more readily crack what should have been a highly secure key.
Conclusion
To summarize, cryptography is more crucial than ever in the age of the digital revolution. Although there are many ways to protect data, encryption is one of the best. It helps the user to protect their data from the public or anyone who might use it maliciously.
Even though access to digital information has significantly increased in recent years, individuals and organizations are concerned about the potential for cyber threats and attacks. Therefore, it becomes essential to employ cryptography protocols and understand them frequently.
We hope you found this article interesting and helpful.
People are also reading: