Earlier, in the 1960s and 1970s, vendors that developed computer systems had their own set of protocols. As a result, the communication between computer systems developed by different vendors became extremely challenging.
In order to enable interoperability between computer systems from different vendors, there came the OSI model. It is a conceptual model that defines the standard set of rules for communication between computer systems. The primary objective of this model was to facilitate interoperability among computer systems using a standard communication protocol.
Through this blog post, we shall help you gain a better understanding of the OSI model, its different layers, advantages, and disadvantages.
So, let us start our discussion!
What is an OSI Model?
OSI stands for Open Systems Interconnection. It is a conceptual model that describes the standard protocols or rules that every communication system has to follow while communicating with other systems. In simple words, it is a reference model that provides a standard for different computer systems to communicate with each other.
This model was the first standard model for network communication. Also, it was regarded as the universal language for computer networking. All the major computer and telecommunication companies embraced it in the early 1980s.
The primary idea of the OSI model is to split the flow of data in a computer system into seven different abstraction layers, with each layer stacked over the other. The seven layers of this model are Application, Presentation, Session, Transport, Network, Data Link, and Physical. In addition, each layer has its own well-defined functions and is responsible for communicating with immediate lower and upper layers.
Today, the modern internet does not strictly follow the OSI model. Instead, it is based on the TCP/IP model or the Internet Protocol Suite .
Though the Open System Interconnection model is not widely in use today, it is still helpful in troubleshooting complex networking issues. This model breaks down the networking issue and isolates the source of that problem. The primary idea is to narrow down the problem to one specific layer of the model, which eliminates unnecessary tasks and makes troubleshooting easy.
History
In the late 1970s, the development of the OSI model began with the need to enable data transmission between different communication systems. In the 1980s, the Open Systems Interconnection group made this model a functional product at the International Organization for Standardization (ISO).
Before the advent of this model, the networking was either sponsored by the government, such as ARPANET in the US, NLP network in the UK, etc., or developed by vendors with their own standards, such as IBM's Systems Network Architecture.
At the beginning of 1977, the International Organization for Standardization (ISO) conducted a program to discuss and develop standards and methods of networking. At the same time, the International Telegraph and Telephone Consultative Committee (CCITT) was working on the same to develop the standards of networking.
Both these bodies created a draft of their networking models, and interestingly, both drafts were closely similar. Later, in 1983, both the bodies, ISO and CCITT, decided to merge their drafts and published ‘The Basic Reference Model for Open Systems Interconnection’ in 1984. Today, we refer to it as the Open Systems Interconnection Reference Model, the OSI Reference Model, or simply, the OSI model.
Characteristics of OSI Model
The following are the characteristics of the OSI model:
- Application, Presentation, Transport, and Session layers are the upper layers or software layers, while Network, Data Link, and Physical layers are the lower layers or hardware layers.
- The upper layers are close to end-users and primarily deal with the issues associated with an application. In addition, these layers are implemented only in software.
- The lower layers deal with data transport and issues related to it. Data Link and Physical layers are implemented in both hardware and software.
- Each layer of this model is assigned the task of services, interfaces, and protocols.
Advantages of OSI Model
Here are the remarkable benefits of the OSI model:
- It is a generic model and serves as a standard model for communication in computer networking.
- This model is flexible because it distinguishes layers according to services, protocols, and interfaces.
- It has the ability to adapt to many protocols. You can implement any protocol in this model since the protocols are hidden.
- It supports both connection-oriented and connectionless services. Therefore, you can ensure the reliability of communication using connection-oriented services and faster data transmission over the network using connectionless services.
- The administration and maintenance of this model are pretty straightforward and easy since this model distinguishes services into various layers.
- Any changes in one layer do not impact other layers because the architecture of this model follows the abstraction principle.
- Troubleshooting the networking issues is quite simple in this model. Therefore, it becomes easy for network administrators to identify the issue by looking at each layer.
Disadvantages of OSI Model
Some of the significant downsides of the OSI model are listed below:
- This model is entirely theoretical, i.e., the practical implementation is almost impossible. Also, there is no appropriate technology to implement this model.
- It has a complex structure and is difficult to understand.
- There is duplication of services, such as flow control, addressing, and error control, in various layers of this model. In short, there is no optimization of layers.
- The session and presentation layers in this model have limited functionalities.
- There is interdependence among layers. Meaning that layers are not able to function in parallel. Unless a layer does not receive data from its previous layer, it is not able to function.
Layers of an OSI Model
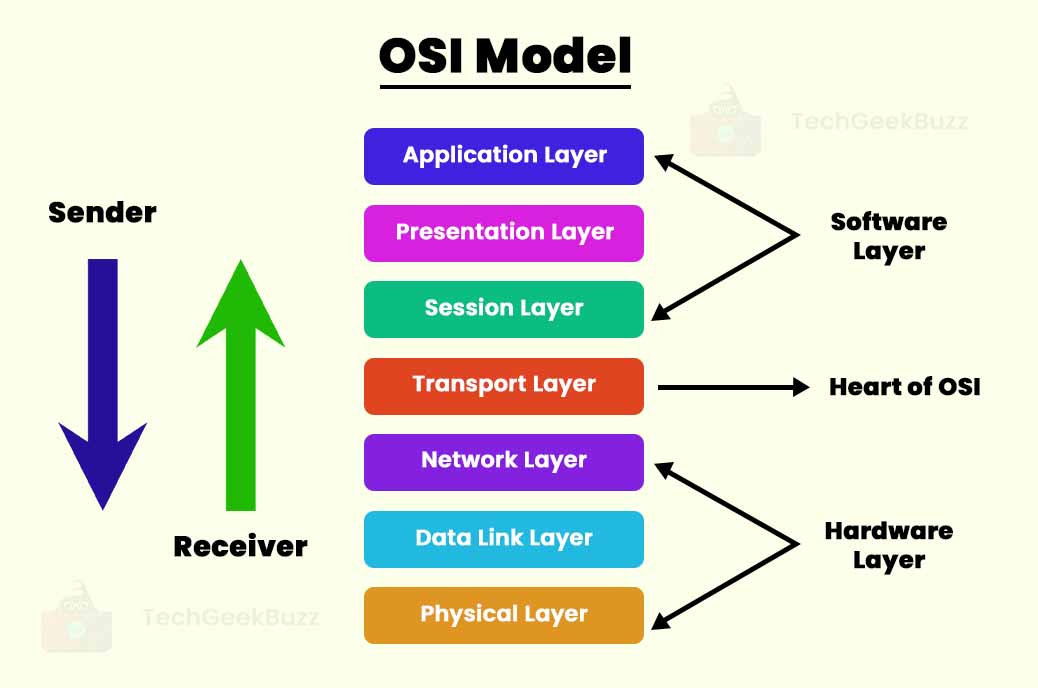
The following are the seven layers of the OSI model, along with their descriptions and functions:
-
Physical Layer (Layer 1)
The physical layer is the lowest layer of the OSI model. It establishes the actual physical connection between devices. The information in this layer is in the form of bits. Also, the primary function of this layer is to transmit bits from one node to the next over a network. The following are the functions of the physical layer:
- Bit Synchronization: The physical layer provides a clock that manages the synchronization of bits. This clock enables synchronization between the sender and the receiver at the bit level.
- Bit Rate Control: This layer also manages the transfer rate, i.e., the number of bits sent per second.
- Transmission Mode: The physical layer is also responsible for defining the transmission mode, such as simplex, half-duplex, and full-duplex, between two connected devices.
- Physical Topologies: Physical topologies define how various nodes or devices in a network are arranged. Star, bus, mesh, and ring are popular network topologies.
Some popular physical layer or layer 1 devices are repeaters, hubs, modems, and cables.
-
Data-Link Layer (DLL) (Layer 2)
The layer above the physical layer is the data link layer. The primary function of this layer is to ensure that there is error-free data transmission between two nodes. In addition, it is responsible for transmitting the data packets to the host using their MAC addresses, whenever they arrive in the network.
Note: Packets in DDL are primarily referred to as frames.
Furthermore, there are two layers in the data link layer, namely logical link control, and media access control.
-
Logic Link Control (LLC) Layer
This layer is responsible for transmitting data packets or frames to the receiver’s network layer. Moreover, it identifies network protocols, performs error checking, and synchronizes the frames.
-
Media Access Control (MAC) Layer
This layer acts as a bridge between LLC and the physical layer. It uses MAC addresses to connect devices and transfer packets over the network. The following are the key functions of the data link layer:
- Framing: Framing implies translating the raw bitstream from the physical layer into frames. DDL adds a header and trailer to a frame, where the header consists of the source and destination addresses.
- Physical Addressing: Once this layer creates frames, it adds the physical addresses (MAC addresses) of the sender and the receiver in the headers.
- Error Control: This layer provides the function of detecting damaged and lost frames and retransmitting them over a network.
- Flow Control: It is important to have a constant data rate on both sides, the sender and the receiver. Otherwise, there are chances of data corruption. The flow control mechanism ensures that the transmitting station, such as a server, with a higher processing speed, does not exceed the receiving station with a lower processing speed.
- Access Control: When there is a single communication channel between two or more devices, the MAC layer of the data link layer determines which device has control over the communication link at the given time.
Switches and bridges are the data link layer or layer 2 devices. In addition, the network interface cards (NICs) and device drivers of host machines are responsible for handling this layer.
-
Network Layer (Layer 3)
Data transmission from one host to the other host located in a different network takes place in the network layer. It also takes care of routing and forwarding the data packets. Meaning that it determines the shortest path from the number of routers available to transmit data packets. Moreover, this layer manages device handling and tracks the location of devices on the network.
The following are the functions of the network layer:
- Routing: Routing determines the best optimal path from all the available paths to transmit data packets from the source to the destination.
- Addressing: Addressing helps to identify the devices on the network. The network layer adds the addresses of the source and destination to the header of a frame.
- Internetworking: Internetworking provides a logical connection between two devices.
- Packetizing: Packetizing implies encapsulating data received from the upper layers of the network into packets.
Routers are the network layer or layer 3 devices.
-
Transport Layer (Layer 4)
The transport layer ensures the end-to-end delivery of data. In other words, it ensures that the messages are transmitted in the same order as they are sent, without any duplication of data. This layer receives data from the upper layer and converts it into segments.
We can refer to the transport layer as an end-to-end layer because it provides the point-to-point connection between the source and the destination for reliable data transmission. It also acknowledges the successful data transmission and retransmits data in case of errors.
The following are the functions of the transport layer:
- Segmentation and Reassembly: The transport layer divides the data it receives from the upper layer into multiple segments. Also, it assigns a number to each segment. When the segments are received at the destination, the transport layer reassembles them to form a complete message.
- Connection Control: This layer provides connectionless and connection-oriented services. In the connectionless services, each segment acts as an individual packet, and all the segments take a different route to reach the destination. On the other hand, a connection-oriented service establishes a connection with the transport layer of the receiver’s network and ensures that all the segments take a single route to the destination.
- Service-Point Addressing: The transmission of data from the source to the destination is not only from one computer to another but also from one process to the other. The header of the transport layer includes an address called the service-point address or port address. This address ensures that the message gets delivered to the correct process on the computer.
-
Session Layer (Layer 5)
The session layer is responsible for establishing a connection between communicating devices. Also, it controls the maintenance of sessions and authentication and security of communicating devices.
Here are the functions of the session layer:
- Synchronization: While transmitting data, the session layer adds some checkpoints known as synchronization points in the data. This is because if any error is encountered during data transmission, the transmission takes place again from the nearest checkpoint. All this process is called synchronization and recovery.
- Dialog Controller: A dialog controller enables the communication between two systems in half-duplex and full-duplex mode.
-
Presentation Layer (Layer 6)
The presentation layer is responsible for ensuring that the syntax and semantics of data being transmitted between two systems are correct. In addition, it acts as a data translator for a network. Therefore, this layer is also referred to as a translation layer. Moreover, this layer converts the data in one presentation format into another format.
Here are the major functions of the presentation layer:
- Translation: Data transmission between two systems involves the exchange of data in the form of numbers, strings, etc. Since different computers use different encoding methods, the presentation layer is responsible for managing the interoperability between different encoding methods. In simple terms, it converts the data from the sender-dependent format into a common format and then into the receiver-dependent format.
- Encryption/Decryption: Data encryption implies converting the plain data into another format called ciphertext. On the other hand, data decryption means converting the ciphertext into plain data.
- Compression: Data compression reduces the number of bits to be transmitted over the network. It is very important when sharing multimedia files, such as audio, video, and text files.
-
Application Layer (Layer 7)
The application layer is the topmost layer through which users and applications can access the network and various network services. In addition, it requests data from the presentation layer and displays it to the end-users.
Some major functions of the application layer are as follows:
- File Transfer, Access, and Management (FTAM): The application layer allows users to access, retrieve, and manage files in a remote computer system.
- Mail Services: This layer provides email forwarding and storage facilities.
- Directory Services: A directory service is a collection of software and processes that stores, retrieves, and manages information about objects, such as computer accounts, user accounts, mail accounts, and resources available on the network.
Difference Between OSI and TCP/IP
The following table highlights the differences between OSI and TCP/IP models:
| OSI | TCP/IP |
| OSI stands for Open System Interconnection. | TCP/IP stands for Transmission Control/Internet Protocol. |
| The International Standard Organization (ISO) developed this model. | The U.S. Department of Defense developed the TCP/IP model. |
It is a seven-layered model, and these layers are as follows:
|
It is a four-layered model. The following are the four layers of TCP/IP:
|
| The transport layer of this model assures the delivery of data packets to the destination. | The transport layer of this model does not guarantee the delivery of data packets to the destination. |
| It follows a vertical approach. | It follows a horizontal approach. |
| There are separate presentation and session layers. | The application layer includes both presentation and session layers. |
| It serves as a reference model through which you can build various networks. | TCP/IP is an implementation of the OSI model. |
| The network layer of this model provides both connectionless and connection-oriented services. | The network layer of this model only provides connection-oriented services. |
| It properly distinguishes services, interfaces, and protocols. | It does not distinguish services, interfaces, and protocols. |
| This model is protocol-independent. | TCP/IP is protocol-dependent. |
Conclusion
The Open System Interconnection (OSI) model is a conceptual model that guides vendors across the globe to create interoperable communication products and software programs. Also, it is a reference model that defines the functions of a networking system.
In this blog post, we have discussed what exactly the OSI model is, its characteristics, advantages, and disadvantages. Also, we have defined the seven layers of the OSI model and the difference between TCP/IP and OSI models.
We hope you find this article helpful in expanding your knowledge of the OSI model. If you have any queries, post them in the comments section below.
Frequently Asked Questions
1. List out the layers of the OSI model.
The following are the seven layers of the OSI model:
- Application layer
- Presentation layer
- Session layer
- Transport layer
- Network layer
- Datalink layer
- Physical layer
2. What is half-duplex communication?
Half-duplex communication is two-way or bi-directional communication. It involves transmitting data in both directions on a single carrier but not at the same time. It means that both the end devices can act as sender and receiver but not at the same time. When one device sends data, the other one receives it, and vice versa.3.
3. What is full-duplex communication?
Full-duplex communication is also two-way or bi-directional communication. In this type of communication, both end devices can act as sender and receiver at the same time.
People are also reading:


![What is TCP/IP Model? [Definition, Working, & Layers]](/media/new_post_images/TCP_IP_Model.webp)
