The introduction of electronic mail in 1971 changed the world of communication forever. The transfer of information became very efficient. Waiting for letters was a thing of the past. And it is entirely reliable. Over time, Email has undergone several upgrades, improving Email overall.
But with this came the form of threats that have troubled security experts for years. One of the most common and harmful cyber threats to email is Phishing.
In this article, we will look at this threat. We will understand what it is, how it is executed, and what measures you can take to protect yourself from this.
What is Phishing?
Phishing is a common technique of social engineering assault in order to acquire user information, such as login passwords and credit card details. It takes place when a perpetrator sends a text message, instant message, or email to the victim while seeming to be a reliable source in order to get them to open it. This may result in installing malware on the recipient's computer, a ransomware attack to lock it down, or releasing personal information.
Phishing is frequently used as a part of a broader attack, like an advanced persistent threat (APT) event, to infiltrate business or governmental networks. In the latter case, personnel are compromised to go over security barriers, spread malware inside a secure setting, or obtain access to protected data.
Phishing Examples
Let's look at some examples of phishing attacks below.
- Cyberattack phishing scams employ a fake Microsoft email that requests a login to restore your data to obtain your Microsoft login information. Scammers make it seem plausible by appealing to your anxiety about locking yourself out of Windows and the applicability of a recent news event.
- Another Microsoft-related fraud used to obtain your credentials is Office 365 deletion notices. The email scam claims that your account has had a significant amount of files deleted. They provide a login link, which allows your account to be compromised.
- Bank Notification: These emails frequently contain a convenient link that leads to an online form where you are prompted to enter your bank information "for verification reasons." Give them no personal data. Call your bank instead and secure your account at once.
- Email for the Contest or Inheritance Winner: If you suddenly win something or receive an inheritance from a family you've never met, try not to be too ecstatic about it. The reason is that the majority of the time, these emails are phishing attempts that demand your personal information in order to "check" your inheritance or send a prize.
- Tax Rebate or Refund: This phishing scam is common because many people pay or are required to pay annual taxes. These phishing emails generally make false claims about your eligibility for a tax refund or selection for an audit. Then it prompts you to complete a tax form or apply for a tax refund, which the con artists use to either steal or sell your money.
These are a few examples of Phishing, but we still need to understand how Phishing works. Let's take a look at that in the next section.
How Does Phishing Work?
Phishing attacks frequently use social networking strategies and Email or other electronic communication channels. Direct messages delivered across social media and SMS are two examples of techniques.
Phishers can use public information sources to learn more about the victim's background, interests, and activities, usually through social media sites, like Facebook, LinkedIn, and Twitter. They typically utilize these sources to find details on potential victims, such as names, job titles, and email addresses. Later, they create a credible email using this information.
Typically, a victim gets a message that seems to have come from a person or group they know. Threat imposters conducted a phishing assault either by a malicious file attachment or links leading to malicious websites. In either case, the objective is to send the victim to a fake website or to install malware on the user's device. Fake websites deceive users into providing sensitive information, including passwords, account numbers, and credit card information.
Although many phishing emails are blatantly forged, cybercriminal organizations are now employing the same strategies that professional marketers use to select the most effective types of messaging.
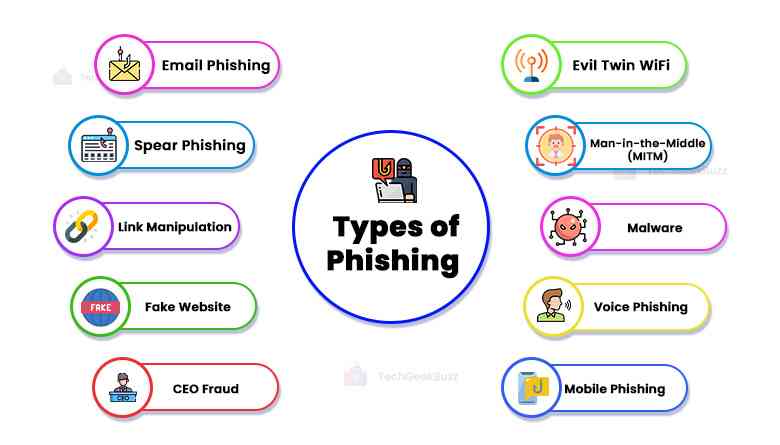
Types of Phishing
So far, we have understood what phishing is and how it works; in this section, we will look at different types of phishing.
-
Email Phishing
The most typical phishing technique is this Email. Many recipients get emails requesting them to reset their passwords, confirm their account details, or update their personal information.
The Email is typically written to convey a sense of urgency, occasionally emphasizing the recipient's need to defend themselves or their company. The email seems to be from a trustworthy source, such as customer service for RBI, Microsoft, a bank, or another well-known corporation.
-
Spear Phishing
Sophisticated email phishing is known as spear phishing. The criminal employs specifically tailored messaging to target a particular person or group and steal information other than personal credit card information. For example, if someone broke in to steal data from a hospital, bank, or other establishments, it would be significantly jeopardized.
-
Link Manipulation
A cleverly crafted email containing a malicious link to any well-known website appears. When the connection is clicked, individuals are directed to a fake website that is made to seem just like the actual website. They are then asked to reform or confirm their account information on the fake website.
-
Fake Website
Hackers create websites that closely resemble popular websites. This fraudulent website, for instance, uses outlook.you.live.com rather than outlook.live.com as its domain. People unintentionally expose themselves to identity theft while on websites they assume to be legitimate.
-
CEO Fraud
Emails sent under the guise of being from the CEO, HR, or a coworker are a typical example of this type of domain spoofing. The Email may request that the receiver supply tax information, confirm an e-transfer, or send money.
-
Mobile Phishing
Mobile Phishing includes, for instance, phony SMS, social media, voicemail, and in-app notifications informing the recipient that their account has been compromised, canceled, or is about to expire. The message, video, or link in the communication aims to steal personal information from the mobile device or infect it with malware.
-
Voice Phishing
When a caller engages in voice phishing or vishing, they highly recommend that the victim contact another number and leave a message or listen to a script. Often, the purpose of these calls is to create a sense of urgency, forcing the listener to act quickly before their bank account is suspended or, even worse, before they risk being charged with a crime.
-
Malware
By opening an email attachment, a user might unwittingly install malware, which is software that scans networks and computers for data. Malware that tracks keystrokes to gather passwords is known as keylogging. Another form of malware that deceives users into providing personal data is a trojan.
-
Man In The Middle
Man-in-the-middle phishing attacks include the deception of two people while they are conversing with one another. The fraudster or criminal may make alterations to the data being sent and received or send each party fictitious requests. The parties involved don't realize a third party controls them since they think they are speaking to each other.
-
Evil Twin WiFi
Making a phony Wi-Fi access point that functions as a genuine Wi-Fi hotspot is possible. This strategy is frequently used in public places like coffee shops, airports, or other areas where Wi-Fi is commonly needed. People connect to this Wi-Fi access point under the impression that they are utilizing the official location, allowing thieves to intercept any data sent over this fictional Wi-Fi account.
Phishing Techniques
Phishing attempts involve more than just sending people an email and hoping they'll click on a bad link or open a malicious document. Attackers trap their victims using a variety of strategies, including:
- We can use Javascript to overlay the address bar of a browser with a picture of a valid URL. Hovering over an embedded link reveals the URL, which can also be modified using JavaScript.
- Numerous popular methods of Phishing involve link modification, often known as URL concealing, in various ways. The easiest method is establishing a malicious URL that appears to be referring to a trustworthy website or webpage while directing users to a harmful web resource.
- Using a URL shortener like Bitly will allow you to hide the link's final destination, whether the abbreviated URLs lead to trustworthy or malicious web resources unknown to the victims.
- Homograph spoofing relies on URLs that match a trusted domain despite having been constructed using different characters. Attackers might, for instance, register domains similar to well-established, well-known disciplines but use slightly different character sets.
- Attackers can occasionally get through phishing protections by rendering all or part of communication as a graphical image. Some security programs will search emails for specific words or phrases frequently used in phishing emails. To get around this, it is necessary to render the message as an image.
- A covert redirect, which results from an open redirect vulnerability that doesn't verify whether a redirected URL points to a reliable source, is a different phishing technique. In that situation, the rerouted URL leads to an intermediary, malicious page that asks the victim for login information. This takes place before sending the victim's browser to the trustworthy website.
Signs Of Phishing
Phishing emails are challenging to discern from legitimate texts. They typically give the impression that they are from a well-known company and may even include corporate logos and other gathered identifying information.
However, there are a number of signs that communication is a phishing effort. These consist of:
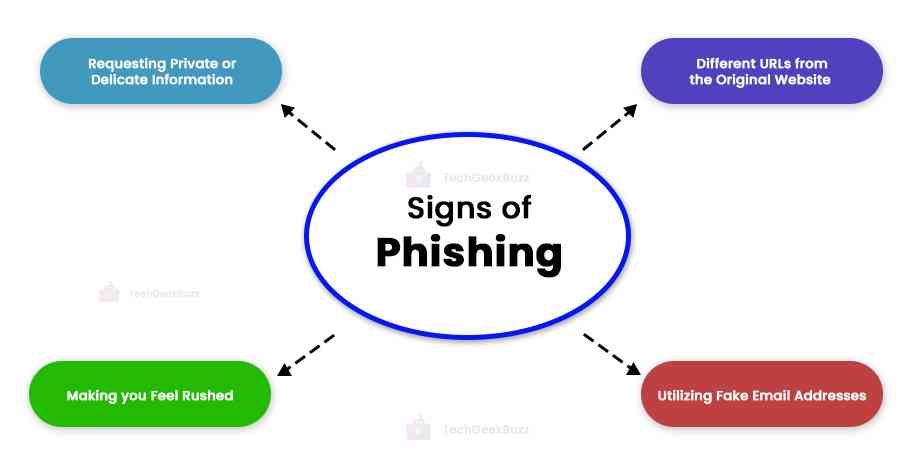
- Requesting Private or Delicate Information: Phishing emails frequently fool you into disclosing confidential information, such as your credit card number or account passwords. They might accomplish this by requesting that you confirm your account credentials or offering a "secure" link that takes you to a spurious website.
- Making you Feel Rushed: Phishing emails frequently make you feel rushed by saying that your account has been compromised or that you must act immediately to avoid a bad outcome.
- Utilizing Fake Email Addresses: Phishing emails frequently use spoofed email addresses that seem to be coming from a robust source, such as your bank or credit card firm. To increase the credibility of their emails, they might also employ the branding and trademarks of a trustworthy company.
- Phishing emails frequently contain attachments or links that take the recipient to websites intended to steal their personal information. Although they may have the same design as the legitimate website, these websites will have different URLs.
You should proceed cautiously when responding to emails with any of these components. To see if there have been any announcements concerning phishing attempts, you may visit the website of the business that the Email appears to be from. Finally, if you want to confirm the Email's validity, you may always contact the company directly.
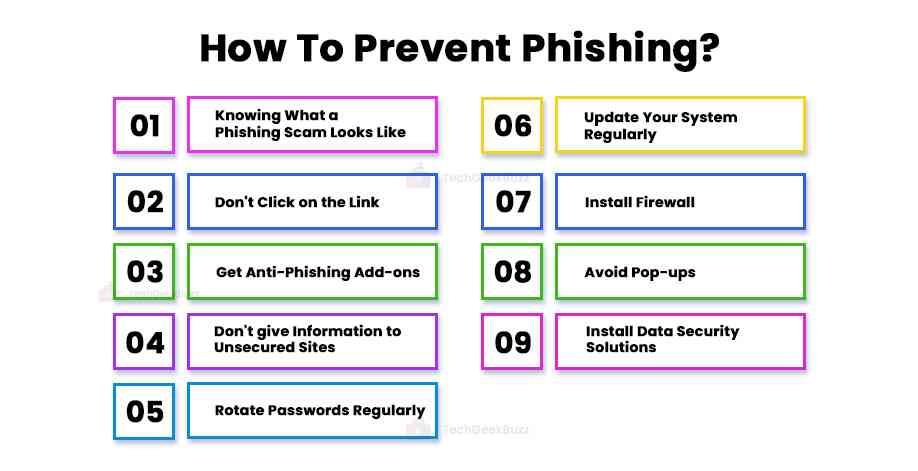
How To Prevent Phishing?
In this section, we will take a look at some standard methods you can use to prevent phishing.
-
Knowing what a Phishing Scam Looks Like
Although new phishing attack techniques constantly evolve, you can find certain shared traits among them all if you know what to look for. Many websites are available online that can keep you informed about the most recent phishing attacks and their particular features. The more frequently you do security awareness training for your users, and the earlier you learn about the current attack techniques, the more likely you are to prevent a prospective assault.
-
Don't Click on the Link.
You shouldn't typically click on links in emails or instant messages, even if you know the sender. At the very least, you should be hovering over the link to check that the destination is the right one.
The destination URL of some phishing attempts can resemble a replica of the legitimate website and be designed to capture keystrokes or collect login and credit card information. You should bypass the link and go directly to the website, if it's possible, through your search engine.
-
Get Anti-Phishing Add-ons
Today, the majority of browsers let you install add-ons that can identify the telltale signs of a phony website or alert you to well-known phishing websites. There is no reason not to have this installed on every device in your company since they are typically entirely free.
-
Don't give Information to Unsecured Sites
If the URL doesn't start with "HTTPS" or if you can't see a closed padlock icon next to the URL, avoid entering sensitive information or downloading files from that website. It may not be the intention of sites lacking security certificates to engage in phishing scams, but it's better to be cautious than sorry.
-
Rotate Passwords Regularly
Make it a practice to regularly update your passwords if you have any online accounts to prevent hackers from gaining unfettered access. Even if you weren't aware that your accounts had been compromised, you may thwart continuing assaults and prevent potential attackers from accessing your accounts by providing an extra layer of security through password rotation.
-
Update Your System Regularly
It can be annoying to receive update alerts constantly and tempting to delay or disregard them. Avoid doing this. The purpose of security updates and patches is to close security gaps in order to stay up to date with modern cyber-attack techniques. If you don't update your browser, you can be at risk for phishing assaults that might have been easily avoided by leveraging known security holes.
-
Install Firewall
Firewalls efficiently thwart external attacks by serving as a barrier between your computer and an intruder. Desktop and network firewalls can boost security and reduce the possibility of hackers infiltrating your environment when used together.
-
Avoid Pop-ups
Pop-ups aren't only bothersome; they're often linked to viruses because of phishing attacks.You may now download and set up free ad-blocking software, which will instantly stop the bulk of harmful pop-ups from appearing on most browsers. However, if one manages to bypass the ad-blocker, fight the impulse to click! Always try to look for a "x" in the corner as pop-ups occasionally attempt to fool you by concealing the "Close" button in a different area.
-
Disclose Information only When You Must
As a general guideline, you shouldn't willingly give up your card information unless you completely trust your website. If you want to disclose your information, confirm the legitimacy of the website, the legitimacy of the company, and the website's security.
-
Install Data Security Platforms To Track Signs Of Such Attacks
It's critical that you can recognize and respond quickly to phishing attacks in case you are unlucky enough to fall prey to one. A data security platform helps the IT/Security team by automatically alerting them to odd user behavior and unlawful file modifications. If an attacker gets access to your sensitive information, data security platforms can help you find the compromised account so you can take action to prevent additional damage.
Conclusion
In this blog, we have covered everything related to phishing, the threats it poses, the types of phishing, and how to safeguard against it so that you make an informed choice in protecting your data and business.
As businesses are shifting more and more on the online platform, they need to be aware of these threats and improve their operational strategy. New difficulties in balancing security and productivity levels occur, and they should find measures to secure their data. Understanding how contemporary companies can implement the best methods to protect their data and prevent any malicious activities.
People are also reading:
![What is Phishing? [Examples, Working, Types, and Techniques]](/media/new_post_images/What_is_Phishing.webp)



Leave a Comment on this Post